...
| Code Block | ||
|---|---|---|
| ||
logs ---- gc-core.log.0 ---- gc-core.log.1 ---- gc-core.log.2.current |
CVE-2021-44228 vulnerability
CVE-2021-44228 vulnerability in Apache log4j library cannot be exploited on WCS server. The logger can be configured via log4j.properties only, so attacker must have access to server file system. The vulnerability cannot be exploited via input fields etc. Let's check:
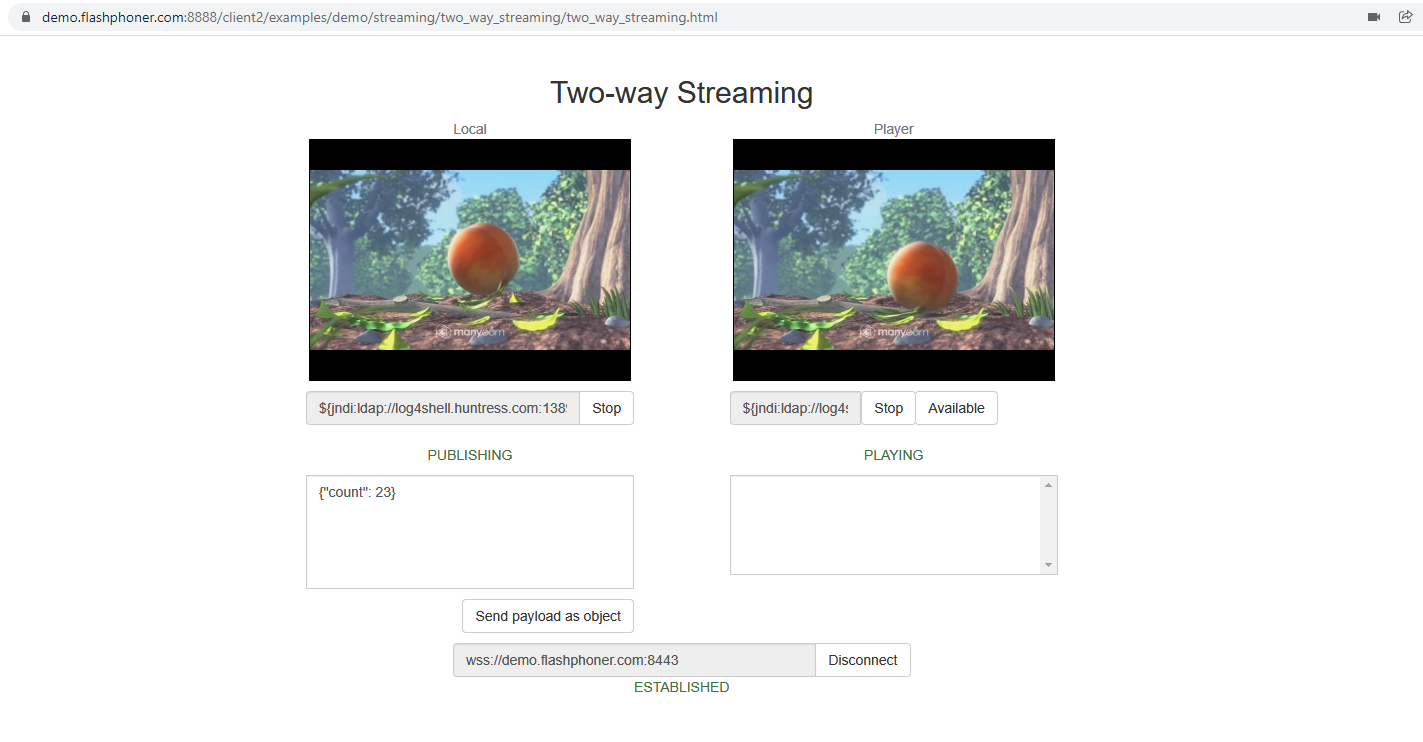
1. Use the URL https://log4shell.huntress.com/ to check the server. This page will generate an unique link to insert to a web page input fields
2, Open Two Way Streaming example page on demo server https://demo.flashphoner.com:8888/client2/examples/demo/streaming/two_way_streaming/two_way_streaming.html, click Connect and insert the test link to stream name fields. Publish and play a stream:
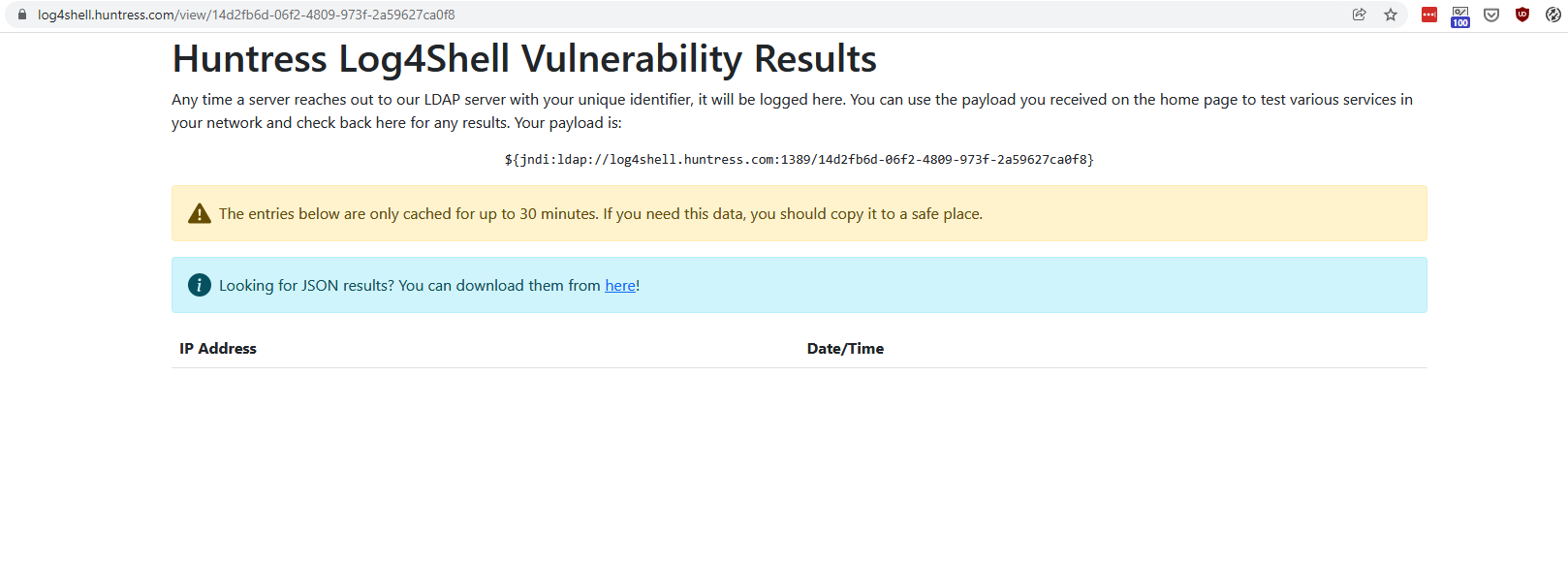
3. Open a special link to view test results. If vulnerability is exploited, IP address and Date/Time columns will show connections from tested server
As test shows, the CVE-2021-44228 vulnerability cannot be exploited in latest WCS build 5.2.1109